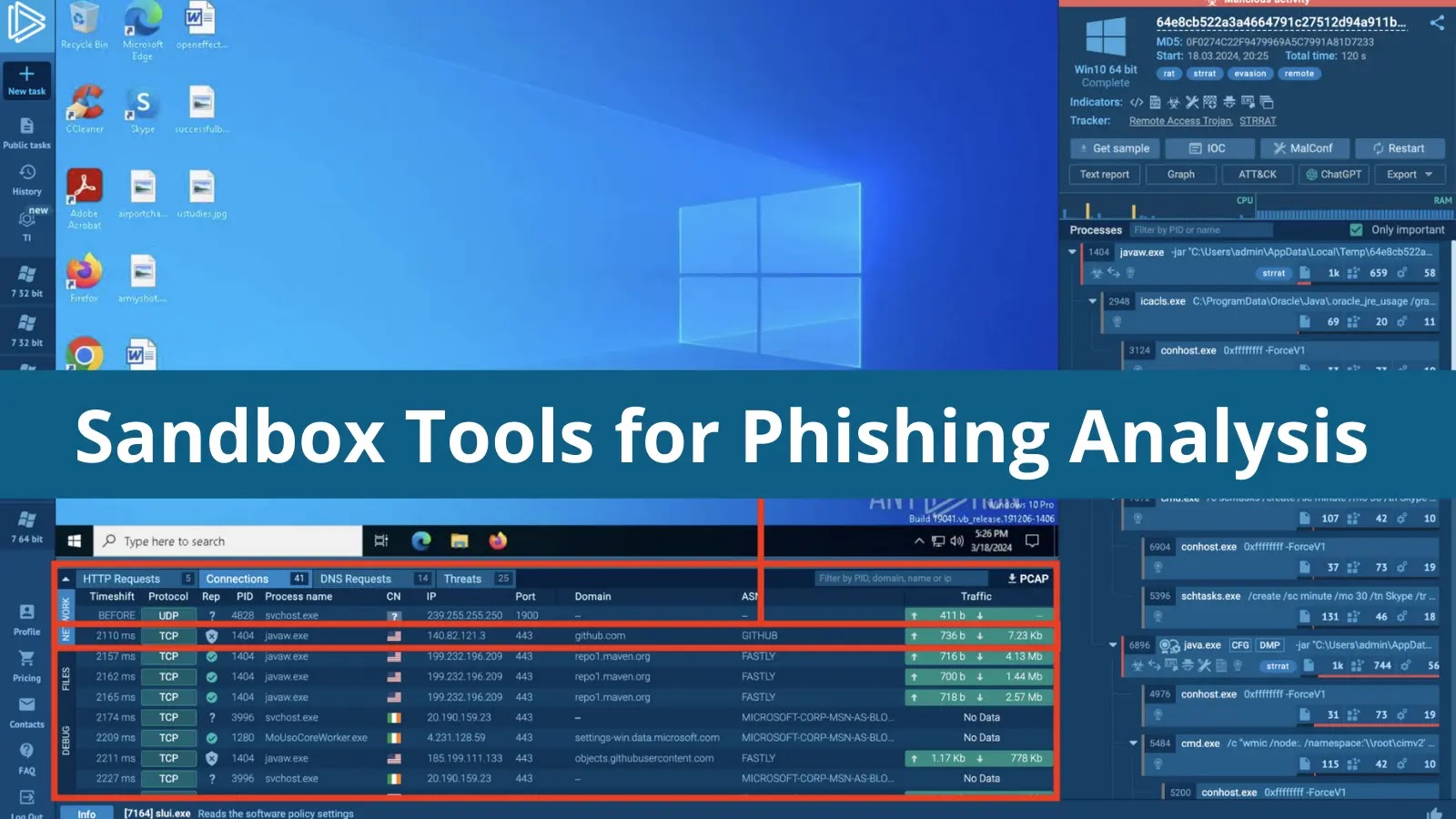
There is a wide variety of solutions one can use to investigate phishing attacks. Yet, in most cases, analysts can do with just one, a malware analysis sandbox. Thanks to its combination of static and dynamic capabilities, a sandbox is well-equipped to tackle the most complex phishing threats out there. Check out these five sandbox tools you can use in your work.
Interactivity
For complex phishing attacks, a sandbox can offer interactivity. ANY.RUN provides complete control over the virtual machine. This allows analysts to manually investigate phishing attacks by directly engaging with them, including by:
- Clicking on links
- Copying/pasting info to/from the VM
- Downloading attachments
- Solving CAPTCHAs, etc.
Analysts can also open password-protected archives that are often sent as attachments in phishing emails to access their contents in a safe virtual environment.
The interactivity feature lets analysts observe and analyze the malware’s behavior in response to their actions. This gives valuable insights into the attacker’s tactics.
Example:
In this sandbox session, we can observe a phishing attack that uses a chain of redirects to avoid detection by security systems. It starts a TikTok link redirecting to a Google AMP URL, which ultimately leads to the final phishing page hosted by Cloudflare IPFS.

ANY.RUN’s interactive analysis makes it possible to follow through the entire attack chain and even submit fake credentials. The sandbox shows that the entered data is sent to a malicious domain via an HTTP POST request.
Start analyzing phishing and malware attacks in ANY.RUN - Sign up for a free account!
RSPAMD Integration
RSPAMD is a spam filtering system designed for evaluating the spam level of emails. It does this by assigning a score to each analyzed email. The ANY.RUN sandbox integrates this tool, making it possible to not only assess the potential phishing threat but also study the elements that make up these emails, including headers, content, and attachments.
With a transparent view of the email’s structure, analysts can obtain a comprehensive understanding of the risks it poses.
Example:
In this session, RSPAMD’s score gives a general idea of the analyzed email’s nature. Since it is above 20, the email likely belongs to the spam category.
The module also highlights the presence of base64-encoded text parts, a short HTML part with an image link, excess whitespace in the “From” header display name, and an unknown client hostname. All these details can help an analyst better understand the threat.
Suricata Rule Engine
Suricata is an intrusion-detection system equipped with advanced capabilities for identifying phishing and malware attacks. ANY.RUN’s Suricata engine matches any phishing-related activity to the existing signatures and presents all the triggered rules to the user.

Analysts can also see the content of the rule to get a clear picture of its mechanics and copy it to further enrich their security systems. The Suricata rule engine is continuously updated, including with rules for the latest phishing attacks.
Example:
In this sandbox session, we’re looking at the analysis of a phishing attack where the user is expected to enter their credentials on a fake form that looks similar to the one they use at work.
One of the triggered Suricata rules displays a message about this fake authentication page and provides details about the source and destination IPs/ports and protocol information.
MITRE ATT&CK Matrix
The MITRE ATT&CK Matrix is the industry standard for analyzing and categorizing the Tactics, Techniques, and Procedures (TTPs) of cyber threats.
The ANY.RUN sandbox maps the TTPs found in different phishing attacks to the framework, helping analysts to understand the attacker’s methods and motivations. The tool also provides a common language for discussing and analyzing cyber threats, promoting collaboration and knowledge sharing among analysts.
Example:
During this sandbox session, a phishing attachment in the form of a .zip archive was submitted for analysis. Upon examination, the sandbox detected the presence of Remcos, a remote access trojan (RAT), exposing the malicious activities of this malware.
With the MITRE ATT&CK matrix, it is easy to see and learn about the specific tactics, techniques, and procedures (TTPs) that the threat used during its execution.
Phishing Tag
The “phishing” and “spam” tags allow analysts to easily identify and categorize potential threats.
This feature is particularly useful when handling large volumes of emails, where quick identification of phishing attempts can significantly reduce the risk of a successful attack.
Example:
Tags help analysts quickly determine if the sample poses a threat
In this analysis session, the sandbox displays the results of an .eml file analysis with the “spam” and “phishing” tags.
It also indicates that the sample exhibits “Malicious activity.” Based on this information alone, users can make a decision on how to proceed further in relation to the email.
Bonus: Investigating Phishing Attacks
In addition to a sandbox, ANY.RUN lets analysts conduct investigations into phishing attacks and other threats with the help of the Threat Intelligence Lookup portal.
The service makes it possible to conduct advanced search using over 30 indicators, such as IPs, TTPs, and even command line fragments. The results reveal more context about the threat, including related indicators and interactive analysis sessions in the sandbox where these indicators were identified.
The portal relies on the threat information extracted from the ANY.RUN sandbox’s public database of malware and phishing samples, which receives thousands of fresh uploads daily from users around the world.
This means that analysts have access to the information on the current threat landscape.
Example:
To demonstrate, let’s use a query to gather information about recent phishing attacks designed to deceive users into revealing their passwords. The query is composed of the following components:
- Task type and threat level: We’re searching for all instances of URLs analyzed in the sandbox within the past 14 days that have been flagged as malicious.
- URL element: This part of the query focuses on URLs containing the “@” symbol, which is often employed in phishing links with pre-filled email addresses.
By running this query, we can uncover a wealth of contextual information from analyses that match our criteria. This data includes associated IPs, domains, and the analysis sessions themselves, providing valuable insights into the latest phishing threats.
Start Using ANY.RUN Today
The ANY.RUN sandbox simplifies phishing and malware analysis, providing conclusive results in under 40 seconds.
You can check out how ANY.RUN’s features, including the private team space, all Windows VMs, and advanced analysis environment settings, can improve your work.